
Register Here
In-person: 1420 N. Charles St.
Baltimore, MD 21201
Location: 1420 N. Charles St.
Baltimore, MD 21201
Duration: 3 Days
Date: 06/27/2023 – 06/29/2023
Time: 8:00 AM – 5:00 PM Eastern
This course covers basic intelligence writing and briefing principles as well as methods for effective and clear intelligence sharing. Topics include creative and critical thinking, critical reading skills, source evaluation,
» Read more

Register Here
Live Online
Duration: 3 Days
Date: 06/27/2023 – 06/29/2023
Time: 8:00 AM – 5:00 PM Eastern
This course covers the acquisition, examination, and analysis of many types of financial records, including bank statements and checks, wire transfer records, and business records. Topics include recognizing and investigating common indicators of fraud, using spreadsheets to facilitate analysis and pattern recognition, and financial profiling. There is a strong focus on presenting financial evidence in multiple modalities: spreadsheet data outputs,
» Read more

Register Here
June 27-28, 2023, 10am-2pm (EST) with an hour lunch break
Live online (via Zoom)
Chat rooms, discussion forums, and VoIP, instant messaging, and social media platforms have been used to facilitate cyber-enabled fraud, such as the sale of stolen data, skimming, and BEC scams. This webinar introduces participants to cyber-enabled fraud, types of cyber-enabled fraud, and the platforms used in the commission of these types of cybercrime.
» Read more

Register Here
May 30-31, 2023. 10am-3pm with an hour lunch break
This introductory course familiarizes participants with illegal darknet markets and associated forums, particularly the illicit goods and services offered, as well as successful law enforcement operations targeting these sites. Participants will gain practical knowledge, skills, and abilities (KSAs), including how to access the darknet, create anonymous accounts, enact operational security, and how to apply these KSAs to conduct darknet investigations.
» Read more

Register Here
Billions of dollars are being stolen from elder victims each year. While the scammers are mostly overseas, there is a black-market economy of gift cards, cash, and cryptocurrency flourishing within the U.S. Sadly, when the thousands of victims each year report these crimes to the police, they are told, “Sorry, there is nothing we can do.” The San Diego Elder Justice Task Force (EJTF) set out to answer the question of,
» Read more
Register Here
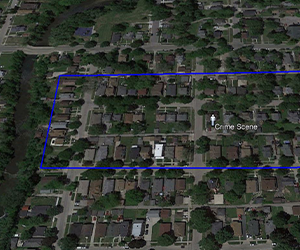
Back by popular demand. This webinar will cover how to properly write search warrants for Google Geofence data and how to interpret the data. The presenter will discuss a walk through of each stage of the process, use of forensic mapping tools to help analyze the Google data, and real cases on obtaining and analyzing Google Geofence data.
This webinar will not be available on-demand.
Presented by:
Jeffrey German,
» Read more

Register Here
Let’s face it- pain management with medication and surgery is not always effective and definitely not a long-term solution. This is where nutrition shines! Eating foods that dampen inflammation is one of the most useful and powerful tools you have to reduce and manage pain. In this webinar, you’ll learn what foods fuel inflammation and what foods extinguish it. Walk away from this webinar with practical nutrition strategies you can implement today to get you out of pain and feeling your best.
» Read more

Register Here
April 3-4, 2023 10am-4pm
This course covers one type of “crime as a service” (CaaS) offered on clearnet and darknet spaces, namely malware as a service (MaaS). Specifically, this course introduces participants to MaaS, the clearnet and darknet sites where malware and MaaS are marketed, advertised, and sold, and information about them is distributed. Particularly, attention will be paid to the M.O., tactics, targets, and tools used by perpetrators of this cybercrime.
» Read more

Register Here
April 10-11, 2023 10am-4pm
This course covers one type of “crime as a service” (CaaS) offered on clearnet and darknet spaces, namely malware as a service (MaaS). Specifically, this course introduces participants to MaaS, the clearnet and darknet sites where malware and MaaS are marketed, advertised, and sold, and information about them is distributed. Particularly, attention will be paid to the M.O., tactics, targets, and tools used by perpetrators of this cybercrime.
» Read more

Register Here
April 13-14, 2023 from 10 a.m. to 4 p.m. EST with an hour lunch break.
Chat rooms, discussion forums, and VoIP, instant messaging, and social media platforms have been used to facilitate cyber-enabled fraud, such as the sale of stolen data, skimming, and BEC scams. This course introduces participants to cyber-enabled fraud, types of cyber-enabled fraud, and the platforms used in the commission of these types of cybercrime.
» Read more














