Semi-autonomous vehicles have started to enter the market, and fully autonomous vehicles will likely follow. Elon Musk predicts that Tesla will be producing fully autonomous cars within roughly two years (he acknowledges the regulation and safety approval process might take an additional one to two years). Similarly, Toyota plans to launch its first self-driving vehicle by 2020, and Google plans to start commercializing its self-driving car the same year.
Category: Legal
The Difficulties of Litigating Cyber Crime
The past several decades brought many new challenges to law enforcement, particularly due to the emergence of new technology. One such issue is cyber crime, which has been a challenge for law enforcement in both establishing laws against the activity, as well as providing tools for law enforcement officers to combat cyber crime. This article will review some difficulties for law enforcement officers at the state and local level in litigating cyber crimes affecting businesses and private citizens.
Attorney General Kamala Harris to Help Law Enforcement in Investigations of Criminal Invasions of Sexual Privacy
By: Danielle Citron, Lois K. Macht Research Professor of Law, University of Maryland
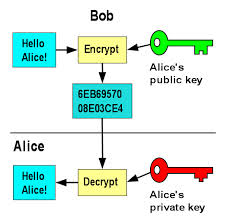
California’s Attorney General Kamala Harris has created a first-of-its-kind online resource designed to assist law enforcement in understanding and investigating crimes related to the cyber exploitation of a person’s nude images in violation of privacy and without consent (also known as nonconsensual pornography). Before discussing the resources created by AG Harris’s Task Force, let me first briefly explain the destruction caused by nonconsensual pornography,
#Greenbirds
On Twitter, the “#” sign refers to a hashtag—a way to group conversations together and make topics of discussion easier to discover and search. Our blog topic of discussion is #Greenbirds—which involves social media influencers on Twitter supporting the Islamic State (also known as ISIS or ISIL).
#Greenbirds: Measuring Importance and Influence in Syrian Foreign Fighter Networks—is a report from London-based researchers at the International Centre for the Study of Radicalisation and Political Violence who are studying foreign fighter networks.
Bots in the Court of Law
What are bots, and why should lawyers be concerned about them? For this blog topic of discussion, bots are considered “a device or piece of software that can execute commands, reply to messages, or perform routine tasks, as online searches, either automatically or with minimal human intervention.” For law enforcement, such bots are an emerging threat because they are being programmed to carry out online tasks that sometimes can cross the line into illegal activities.
Emerging Threats: Cryptolocker

Cryptolocker is financially-motivated ransomware that encrypts a user’s computer files and demands payment in either an anonymous currency (Bitcoin), or Moneypak payment cards. Propagation & Exploit is typically via spam email purporting to come from shipping companies or regarding business processes, dropped by other malware, thumb drives, and Yahoo! Messenger. Upon infection, Cryptolocker contacts the command and control (C2) server for a public RSA-2048 encryption key, which is downloaded and used to encrypt typical enterprise files types,
Emerging threat: CryptoWall
CryptoWall is a digital ransomware that encrypts files on the infected machine and any connected file shares or drives. CryptoWall is distributed through phishing emails, malicious advertisements, compromised web sites, and as fake updates for applications such as Adobe Reader, Adobe Flash, and Java. In June 2014, this malware spread through the RIG exploit kit. Malicious actors use compromised websites to host the RIG exploit kit, which then exploits vulnerabilities in Java, Silverlight, and Flash to deliver the CryptoWall payload to the victim.
Emerging Threat: Telephone Denial of Service (TDoS)
TDoS attacks overload the telephone network, preventing legitimate telephone calls from being placed or received. Attacks against SLTT emergency lines, primarily at public safety answering points (PSAP) such as 9-1-1 centers, but also including utility department emergency numbers and other emergency numbers, remain a continuing threat. There is a relatively low risk of TDOSes occurring, however an attack against a PSAP could endanger emergency responders and citizens if the TDOS prevents them from contacting the PSAP.
Emerging Threats: Point of sale (POS)

POS compromises are increasingly common in the commercial sector but remain rare in the government sector. The POS is the location where money transfers from the buyer to the seller at a retail store. Compromises can include physical tampering with pinpads or cash registers, complicit employees, or computer viruses. The compromise may affect the cash register or the computer that processes the credit card payments, and may target debit cards and pin numbers or credit card information.
Emerging Threat: Doxing

“Doxing” is the publication of personally identifiable information (PII) of someone to the internet, generally for malicious purposes. The kinds of information disclosed may include the victim’s home addresses, family members’ information, and financial information.
Hacktivist groups dox government officials in response to perceived injustices with the objective of embarrassing the victim, or providing the information so others may target the victim for malicious activity. In some cases, organized cyber criminal groups and criminals may take advantage of information released during doxing incidents but are not known to conduct the activity themselves.





